MacBooks are gaining tremendous popularity. They might soon overtake the total computers produced by the largest PC manufacturer. Apple reportedly sold 5.3 million MacBooks in the fourth quarter of 2018 alone. As more people invest in MacBooks, we … [Continue reading]
Nuances of Bandwidth for Both Webmasters and Internet Users
Online bandwidth is the measurement of the amount of digital information that a medium is capable of processing and transferring. Mediums with higher levels of bandwidth are capable of loading the same amount of information more quickly or more … [Continue reading]
Managing vCard Files for Effective Communication and Branding Optimization
vCard is a file format that is used for digital business cards. There are also vCard editors that allow you to create electronic business cards if you do not have one. This format is convenient because it can be attached to emails, can be sent as … [Continue reading]
Eliminating Common WordPress Vulnerabilities to DDoS Attacks
Distributed Denial of Service (DDoS) attacks are serious threats that every website manager must be prepared for. Unfortunately, some of the most widely publicized DDoS attacks have created a number of misconceptions about the risks associated with … [Continue reading]
Securing Your Privacy Against Deep Packet Inspections
Network administrators, cybersecurity analysts and watchdogs use a variety of different tools to monitor Internet traffic. Deep packet inspection is one of the types of tools that has proven to be highly effective over the past few years. However, … [Continue reading]
Identifying and Protecting Against the Most Dangerous Keyloggers
Keyloggers are among the most frightening tools in the hands of a skilled hacker. They are malicious devices or malware applications that enable hackers to capture every keystroke that you type. Most Dangerous Keyloggers You need to be aware of … [Continue reading]
Excel Shortcuts for More Complicated Commands
We previously wrote an article on the benefits of using keyboard shortcuts in Excel. The shortcuts we focused on were used for simple formatting options. However, there are other shortcuts that are valuable for more complicated challenges. You can … [Continue reading]
CleanTalk as Your Weapon against Spam

Are you tired of spam? You aren't alone. It has become a massive epidemic over the past few years. Around 14.5 billion spam messages are sent every single day. Authorities around the world have started taking stricter penalties against spammers. … [Continue reading]
VPN in 2019: Shortcut to Prevent Data Theft and Monitoring
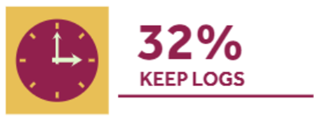
Not all people are in the know about the beneficial functions of Virtual Private Networks. Some users install them to unblock torrenting sites, for example, Demonoid others want to get access to the Canadian Bell content. Yet fewer individuals … [Continue reading]
Navigating the Internet’s VPN Chaos
You don’t have to be a black hat hacker or a dark web dweller to appreciate the benefits of online anonymity. According to a poll from Pew, a plurality of Americans are more concerned about their privacy than ever. Around 57% of Americans don’t want … [Continue reading]