Spotting a phishing email isn’t as easy as one may think these days, and if you’ve ever clicked a link in one of those misleading emails, you’re not alone.
In 2019, 94% of malware was delivered via email and 32% of breaches involved phishing. With phishing attacks more common than ever, many SMEs are looking for IT companies and specialists who offer technology help in tightening up traditional security awareness using cybersecurity training and technology.
There are a lot of things that you can do to help mitigate the risk of phishing attacks, such as improving authentication. Token-based authentication is one type of auth method often used on-prem. Generally, it is a subcategory of MFA (multifactor authentication)
To stop hackers from stealing your information or messing up your network, you should only let people, apps and devices do what they have to do and nothing more. In other words, using the principle of least privilege, you keep your information and network safe and secure.
This article will discuss five common types of phishing attacks, how to detect them — if possible – and how to solve them.
What is a Phishing Attack?
Phishing attacks are when hackers send fraudulent communications that appear to come from a reputable source. These communications may sometimes contain sensitive information about a target, an attachment or a hyperlink – which is then used to collect information about the target. The attachment is almost always malware. Any hyperlink embedded within the communication leads to a website masquerading as a legitimate website.
We’ll get to know how some phishing attacks aim to get personal information from targeted users.
5 Common Phishing Attacks and How to Recognize Them
1. Email Phishing
Cyber criminals send over 150 million phishing emails on a daily basis. This is usually how they start their first phishing trip – targeting a large number of users at a time. Creating an effective phishing campaign doesn’t even require a genius attacker. It takes no more than 7 minutes to generate a phishing email that appears to be sent from a governmental institution of your choice or a corporate organization trusted by the recipient. Such mails may be generated using the Social Engineering Toolkit (SEToolkit) shown in Figure 1.
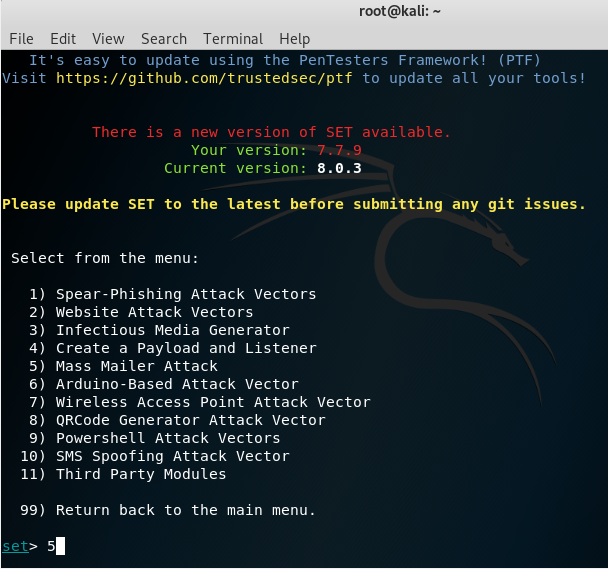
Figure 1. The SEToolkit Framework in Kali Linux
Properly phished emails are difficult to detect, but the easily detectable ones have fake or misspelt domains. Every email address has at least three parts, namely the username, the domain and the top-level domain name as shown in Figure 2.
Most SMEs have their own email server systems and accounts for all users. As an example, legitimate emails from Paypal will have the domain paypal.com. If you receive an email from Paypalsupport@support.com, it’s definitely a phished email and not from Paypal. Whenever you’re unsure, the best way to check an organisation’s domain name is to look it up in a search engine.
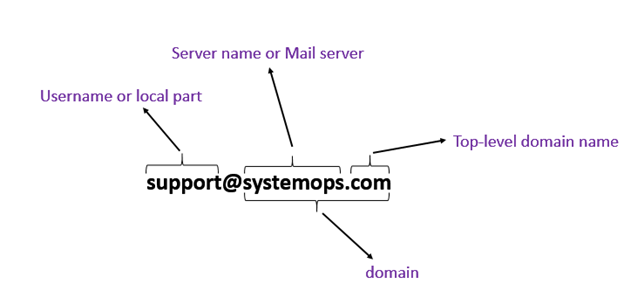
Figure 2. Parts of an email address
2. Spear Phishing
Spear Phishing is an email scam targeted towards a specific individual, business or organization. Attack vectors for spear phishing such as names, email addresses and designation are all available on popular social media sites. Once hackers collect information about their potential target, they craft personalized messages that look authentic enough to convince their targets to freely offer additional personal information such as passwords and bank details. Speared attacks also include attachments and malware links.
Checking the name and email address for a spear-phished email may not be enough. Sometimes, you need to make a phone call to the sender to confirm the legitimacy of the email. If the spoofed email contains hyperlinks, you can verify them by hovering your mouse over those links – which shows the complete address of the link you’ll be redirected to after clicking.
A legitimate MS Word document shared via Google docs should have an address beginning with https://docs.google.com/… as shown in Figure 3. If the shared Google link has an address starting with http://drivef-google.com, it must be a fake link.
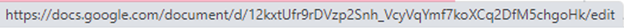
Figure 3. Legitimate address of a shared Google document
When Spear Phishing attacks are directed to the executive members of an organization, it is known as Whaling.
3. Vishing Attack
Hackers implementing this type of attack first gain unauthorised access to the target’s network systems, set up a voice over IP (VoIP) account and then spoof calls to targets. Once they reach their targets, it is easy to give instructions or requests for sensitive information.
It is almost impossible to detect a vished attack if you’re not already familiar with the user whose VoIP account has been hacked. Skilled experts and properly programmed systems are required to detect and block vished attacks.
4. Smishing Attack
Smishing is when an attacker tries to trick its targets into offering their private information via a text or SMS message. Smishing is becoming a major threat in the world of online security, as hackers are using emerging technology to intercept tokens required for multi-factor authentications (MFA). Smishing is a combined form of phishing and text messages in which attackers send SMS containing deceitful links to the victims. Smishing attacks can only be detected using SMS content analyzers, URL filters and Source Code Analyzers.
5. Pharming Attack
Most attackers prefer deploying pharming attacks because they no longer have to trick users into clicking links to a malicious website that appears to be legitimate. In order to achieve this, a pharming attack spoofs the Domain Name System (DNS) of a computer network by placing wrong information in it.
The internet doesn’t actually understand alphabetical addresses like https://www.google.com when you type them into your web browsers. They get translated into numbers known as IP addresses before reaching their destination. The system that does this translation is known as a Domain Name System (DNS). During a pharming attack, the attacker infects the DNS system to translate alphabetical addresses into wrong IP addresses.
After typing a website address, users can hold on until the page fully loads and then carefully inspect the site’s security details. This isn’t an easy task for internet users. Taking extreme precautions such as manually typing in a familiar website address isn’t enough to prevent this type of attack. This is because the misdirection of destination takes place in the DNS system which the user cannot control.
Solution to Phishing Attacks
Phishing attacks are very hard for users and security systems to detect because they are constantly evolving to adopt new techniques. Their success rates can be reduced to a minimum by implementing phishing protection for emails and websites. This solution is never complete without conducting continuous security awareness training for users since they act as the last line of defence.